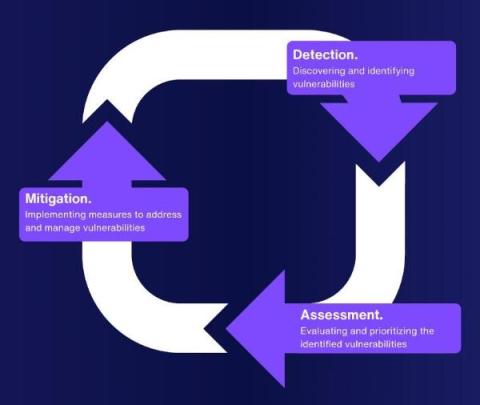
How to Create SIEM Correlation Rules
SIEM (Security Information and Event Management) systems play a crucial role in modern cybersecurity frameworks. They collate log and event data from an array of sources within an organization’s network, facilitating real-time analysis and long-term storage of this crucial information to uphold security standards. A core component of SIEM’s effectiveness lies in its correlation rules, which are designed to detect specific patterns or anomalies that might indicate a security issue.