Container Security: A Quick Overview
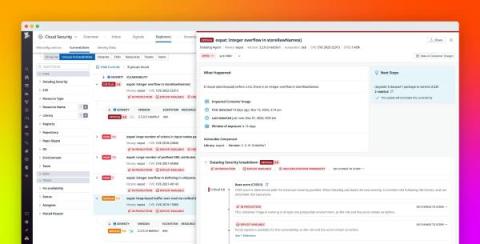
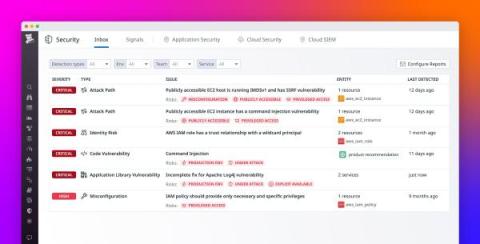
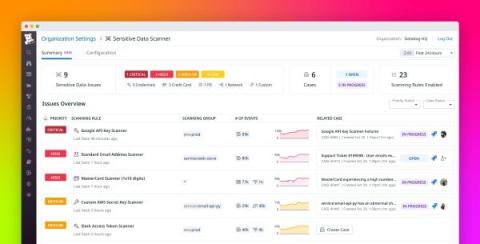
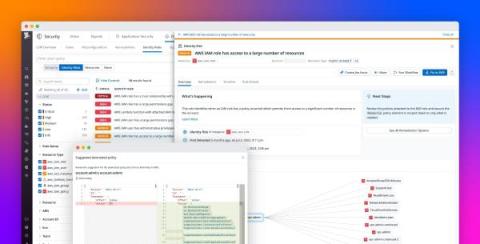
Container security is an increasingly vital aspect of modern software development and deployment. Understanding and implementing effective security measures becomes essential as organizations shift towards containerizing their applications. This article will explore practical insights and strategies for ensuring robust container security. We will delve into some best practices and tools to secure container environments, focusing on securing images and registries, container deployment, runtime security, and more.