Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
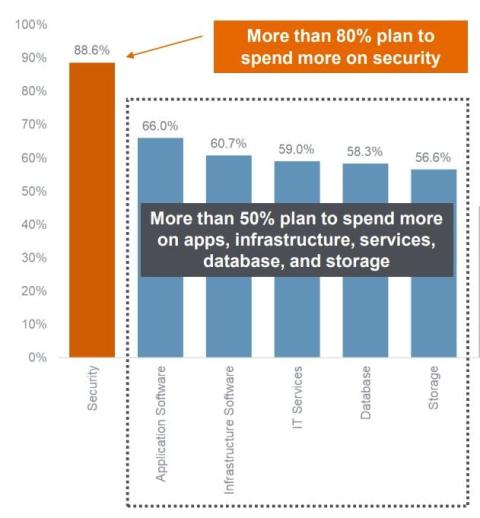
2024 IT Spending Surge: Surprising Insights from Piper Sandler's CIO Survey
Industry analysts Piper Sandler do a yearly 'Industry Note' where they survey CIOs about their next year budget expectations. For 2024 there is a noticeable improvement regarding enterprise IT spending. The header of their survey was: "2024 CIO Survey | Investments in Security, AI, and Cloud Driving IT Rebound". Here is the summary of the full report which is a good read and warmly recommended.
WSJ: "A Hidden Risk in the Municipal Bond Market: Hackers"
December 7, 2023 - The Wall Street Journal has an interesting perspective on K-12 Public schools suffering ransomware attacks. The number doubles between 2021 and 2022 to almost 2,000 a year. Here are a few paragraphs with a link to the full article: "Hacks are on the rise across all industries, but the public sector’s weak protections make it an increasingly attractive target for cybercriminals.
Deepfakes: The New Face of Fraud
Security analysts at identity vendor Sumsub are seeing a massive rise in the use of deepfake fraud in their Identity Fraud Report 2023. And one country may be to blame. While Sumsub’s focus is more around all forms of identity security, it's witnessing a significant increase in deepfakes, as deepfakes are a form of identity fraud. According to Sumsub, the top three fraud trends identified were: The approximate overall growth rate worldwide for the use of deepfakes is 10x.
Russian Hackers Indicted for Phishing Attacks Against U.S. and Allies
The US Justice Department has indicted two individuals for launching spear phishing attacks against the US, the UK, Ukraine and various NATO member countries on behalf of the Russian government. “The indictment…alleges the conspiracy targeted current and former employees of the U.S.
CVE-2023-36553: Critical OS Command Injection Vulnerability in FortiSIEM
Monitor highly regulated workloads with Datadog's FIPS-enabled Agent
Protecting sensitive data from the threat of exposure is a non-negotiable business imperative for organizations, especially those in highly regulated sectors like government and healthcare. To help organizations keep their data secure, the National Institute of Science and Technology (NIST) developed a set of requirements for the hardware and software components responsible for data encryption.
Exposed Server Headers and Cybersecurity Risk
Decoding Essential 8 Compliance: Tanium's Unique path to Success
From Tanium's Australian bureau, we dive into the Essential 8 baseline mitigation strategies and reveal how Tanium's unique architecture goes beyond the traditional approach of other vendors and enables organisations to overcome key challenges to help them successfully achieve automated continuous compliance.
Identity Threat Hunting: How CrowdStrike Counter Adversary Operations Is Leading the Charge
It’s 10:30 p.m. and you’re heading to bed. Unfortunately, a threat actor has your organization in their crosshairs. While you’re brushing your teeth, they’re crafting a social engineering email to pilfer your employees’ credentials. While you’re putting on your pajamas, they’re finding a path to log in. While you’re asleep, is your organization protected?