Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
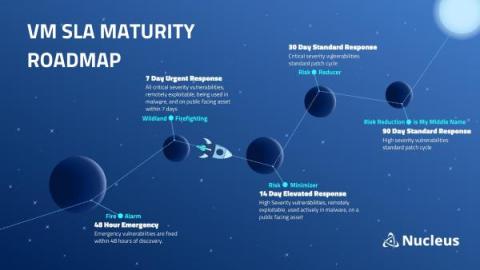
How to Adapt Vulnerability Management Service Level Agreements (SLAs) to Team Maturity
How to Choose the Best Crypto App
Outpost24 Expands Leading External Attack Surface Management Solution with Credential Threat Intelligence
Security warning! All of us are victims of open-source vulnerabilities
Picture this: A user on your network casually explores the internet and scrolls through a website’s comment section. However, a lurking threat known as cross-site scripting (XSS) is poised to exploit vulnerabilities and steal their session cookies, which includes sensitive data such as their logon credentials. But how does this nefarious scheme unfold, and what other open-source vulnerabilities could be exploited in the process?
ShadowIT, Hidden Risk, and the insights that drive action to reduce exposure
Create SBOM on Gradle with the CycloneDX Plugin
3 Tips for Cost Optimization With AWS
As many companies begin to explore the vast capabilities of the public cloud ecosystem, one obstacle continues to be of extreme importance: Cost Optimization. The cloud itself was built for scalability and convenience, but when the most advanced options for your infrastructure can be set up with the touch of a button, a cost friendly migration and ongoing strategy to keep your cloud footprint within budget are key.
KnowBe4 Named a Leader in the Winter 2024 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares security awareness training (SAT) vendors based on user reviews, customer satisfaction, popularity and market presence. Based on 1,455 G2 customer reviews, KnowBe4’s KMSAT is the top ranked SAT platform with 98% of users rating 4 or 5 stars. The KMSAT platform received the highest G2 score among products in the SAT category with a score of 93 out of 100.
Reviewing the Proposed CMMC Regulations: Key Takeaways and Recommendations
The U.S. Department of Defense (DoD) delivered a timely Christmas gift to government contractors and subcontractors last month – the proposed regulations for the Cybersecurity Maturity Model Certification (CMMC) program. After over two years in development, the proposed rule, released on December 26, 2023, aims to enhance cybersecurity compliance across the defense industrial base.