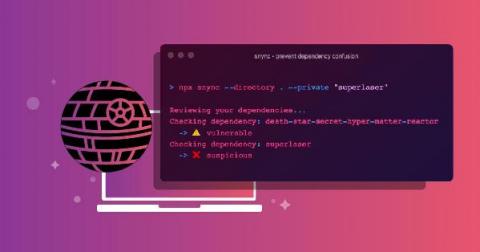
Hunting for Malicious PowerShell using Script Block Logging
The Splunk Threat Research Team recently evaluated ways to generate security content using native Windows event logging regarding PowerShell Script Block Logging to assist enterprise defenders in finding malicious PowerShell scripts. This method provides greater depth of visibility as it provides the raw (entire) PowerShell script output. There are three sources that may enhance any defender's perspective: module, script block and transcript logging.