Rethinking Subjectivity Management for Cyber Insurance
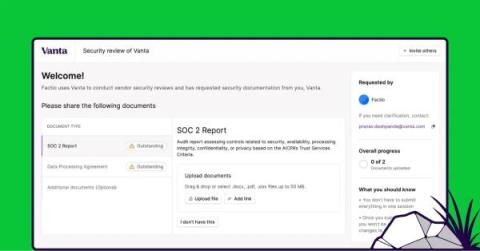
Just like other insurance markets, subjectivities have become a staple of cyber insurance. When a cyber insurance underwriter issues a quote to the broker and insured, there may be additional requirements that must be met before the policy and coverage are activated. The management and resolution of these subjectivities creates friction for all stakeholders involved. It takes longer for insureds to obtain coverage, for underwriters to collect premiums, and for brokers to earn their commission.