How to Conduct a Cybersecurity Risk Assessment for In-Depth Insights
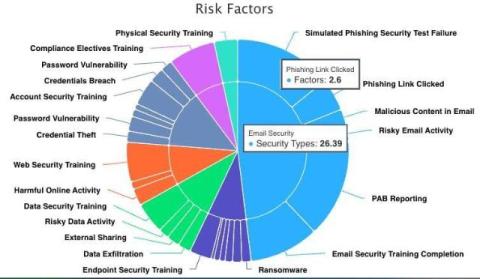
A cybersecurity risk assessment, or cyber risk assessment, is a standardized process that organizations have established along with their implementation of cloud-based technologies to discover the accompanying vulnerabilities and threats. These assessments leverage the available, relevant data to identify the likelihood of various cybersecurity events occurring along with the potential impact should they come to fruition.