CVE-2022-22965: Unauthenticated RCE zero-day vulnerability in Spring Core (Live updates)
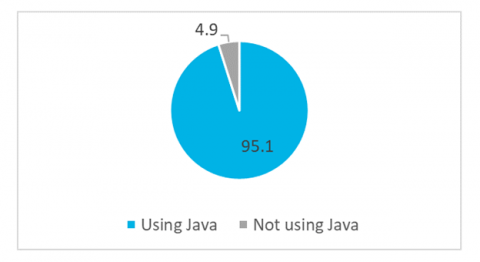
On Wednesday 30th March 2022, news was disclosed online about an unauthenticated RCE zero-day vulnerability in Spring Core, a framework for building modern Java-based enterprise applications.