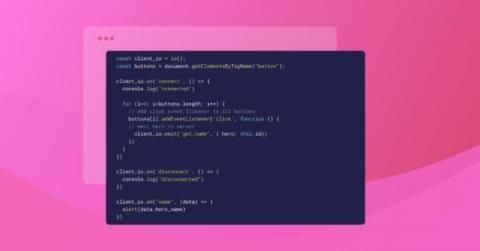
How to build a secure WebSocket server in Python
Typically, when a web app needs something from an external server, the client sends a request to that server, the server responds, and the connection is subsequently closed. Consider a web app that shows stock prices. The client must repeatedly request updated prices from the server to provide the latest prices.