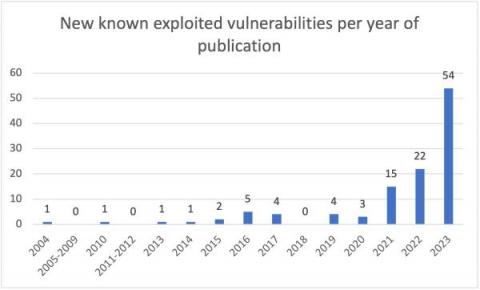
What is Continuous Vulnerability Scanning?
Vulnerability scanning plays a crucial role in safeguarding applications and systems. By utilizing advanced software tools, it detects weaknesses or ‘vulnerabilities’ in computer systems that could be exploited by malicious individuals to compromise the system or steal valuable data.