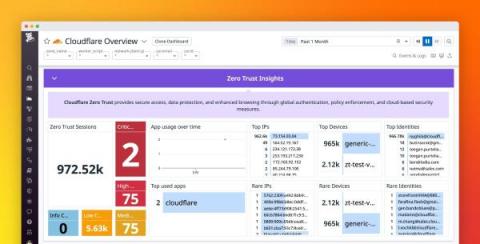
Monitor Cloudflare Zero Trust with Datadog Cloud SIEM
Cloudflare’s SASE is a zero trust network-as-a-service platform that dynamically connects users to enterprise resources, with identity-based security controls delivered close to users, wherever they are. Cloudflare spans more than 300 cities in over 100 countries, resulting in latencies under 50 milliseconds for 95 percent of the internet-connected population globally.