The Problem With Third-Party Breaches: A Data Protection Dilemma
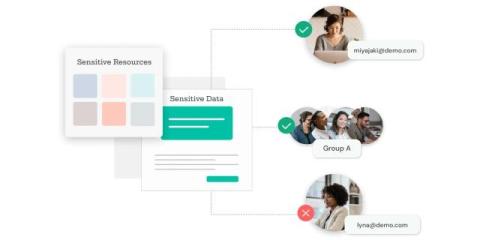
Time and time again, organisations face an escalating threat to their data: Third-party breaches. As businesses increasingly rely on external vendors and partners for various services, the security of sensitive information becomes more vulnerable. This poses the question: Are traditional security measures still effective or obsolete in protecting vital information?