Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
7 Ways to Strike Balance Between Technical Debt and Security Posture in The World of Open Source
Top Five Free and Open Source SIEM
In an age where cybersecurity is paramount, organizations must be vigilant in protecting their digital assets and sensitive information. Security Information and Event Management (SIEM) solutions are crucial in this endeavor, as they provide comprehensive visibility into an organization’s cybersecurity posture. While there are many commercial SIEM tools on the market, the pursuit of truly free and open-source SIEM solutions is gaining traction.
Build a 24/7 Security Operations Center (SOC) with Free and Open Source Technologies
Welcome to our comprehensive guide on building a 24/7 Security Operations Center (SOC) using free and open-source technologies. In the digital age, protecting your organization’s information assets has never been more important. Cyber threats are constantly evolving, and organizations of all sizes and industries are vulnerable to attacks.
Priorities from the OpenSSF Secure Open Source Software Summit 2023
Snyk has been a long-time active participant in and sponsor of the Open Source Security Foundation (OpenSSF). We’re there because we believe in supporting its mission of securing the open source ecosystem. A recent summit meeting convened by the OpenSSF with the White House brought together various US Government departments for a chat about open source security.
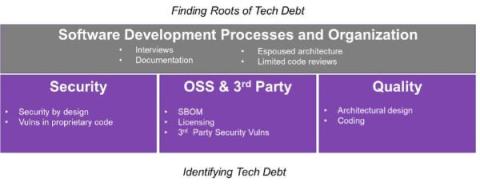
From diligence to integration: How software audits inform post-close M&A strategies
Navigating the Open Source Landscape: Finding Your First Contribution
🕵️♂️ Embarking on your journey and learning how to contribute to open source is an exciting step towards honing your programming skills, collaborating with experts, and giving back to the global developer community. However, the challenge often lies in finding the right project to kickstart your open-source journey.
Is Open Source Software Dead?
Open source software (OSS) has driven technological growth for decades due to its collaborative nature and ability to share information rapidly. However, major OSS security vulnerabilities like Log4j, Heartbleed, Shellshock and others have raised concerns about the security and sustainability of similar projects. At the same time, major open source-based companies have changed their OSS licenses, like MongoDB, Elastic (formerly ElasticSearch), Confluent, Redis Labs and most recently, HashiCorp.
To OSINT and Beyond!
Open-Source Intelligence (OSINT) can be valuable for an organization and penetration testing engagements in several ways. Today, let me highlight two areas: Leaked Credentials and Files. As part of any security engagement, it is ideal, if not essential, that we look up our target’s leaked credentials and files, as many clients do not have a high level of visibility or awareness in this area.