Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Creating a Honeytoken - Complete Tutorial
Honey Tokens or Canary Tokens are credentials designed to alert you when an attacker is in your infrastructure. This is a complete tutorial how to create them using only open-source projects.
Open source software: A pillar of modern software development
Black Duck's New Year's Resolution
The ultimate race condition: Securing open source infrastructure
Top Open Source Licenses Explained
With an understanding of what open source licenses are and their benefits, it’s also useful to know what are the main categories of these licenses, the different types, and their requirements. It’s quite an array, which can be overwhelming, but with this knowledge, you can make more informed choices about what software and what licenses are right for your purposes.
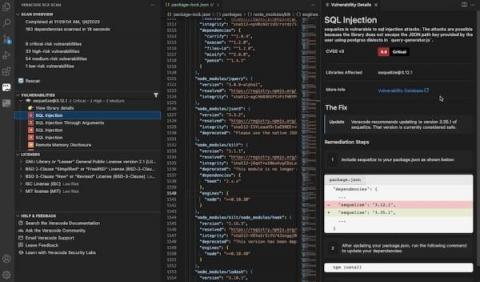
6 Reasons You Need to Run SCA Scans on Projects in VS Code
We love open-source software (OSS). Not only does it save time and effort, but it’s also incredibly rewarding to collaborate with other developers on major projects. Plus, it opens the door for innovation that otherwise wouldn’t be possible at this scale. However, with code comes responsibility, and so it’s imperative to understand the risk OSS libraries carry when we’re integrating them into projects.
CNCF accepts Kubescape as its first security and compliance scanner project
8 Best Secure Photo Apps in 2023
OSPO security evolution: The Kübler-Ross Model of open source
What’s in an OSPO? Open Source Program Offices are popping up all over, in recognition of the facts on the ground: open source software (and I would argue open standards as well) plays an enormous role in building and maintaining the software that increasingly drives the planet.