Prioritizing open source vulnerabilities in software due diligence
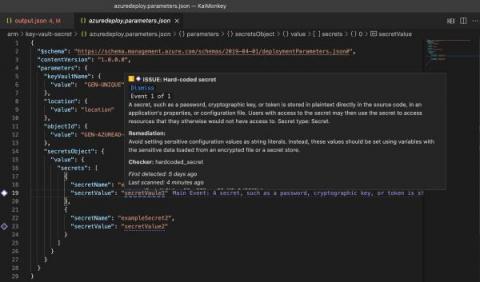
Black Duck Security Advisories provide actionable advice and details about open source vulnerabilities to help you improve your remediation activities. A vulnerability is a software bug that hackers can exploit to attack an application. Ideally, software is written so as to proactively thwart the efforts of bad actors, but that is often not the case.