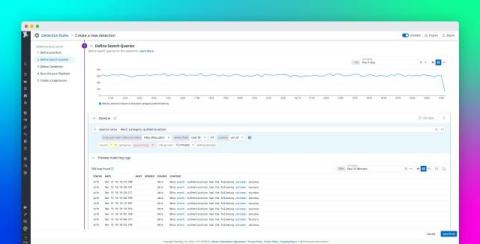
CrowdStrike Falcon Next-Gen SIEM's First Year Transforming the SOC
There are rare moments when technology doesn’t just improve — it leaps forward, leaving behind everything we once thought was enough. The launch of CrowdStrike Falcon Next-Gen SIEM was one of those moments. It’s a game-changer that alters the way security teams think, operate and stop breaches.