Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2023
Micro Lesson: Cloud SIEM Automation Service
How does Elastic Security drive value to your organization?
A Guide to Digital Forensics and Incident Response (DFIR)
Responding to remote service appliance vulnerabilities with Sumo Logic
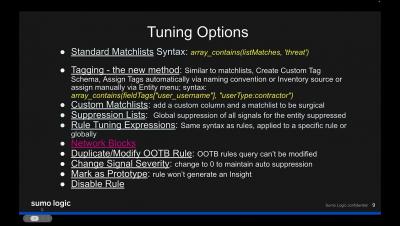
Sumo Logic Customer Brown Bag -- Security -- CSE Rule Tuning -- June 20th 2023
UTMStack SIEM Real Time Detection and Response Powered by AI
What are Advanced Persistent Threats (APT) and How to Prevent Them.
Top 5 SIEM Use Cases CrowdStrike Falcon LogScale Solves Today
SIEMs play a crucial role in the modern SOC: They allow you to collect, correlate and analyze log data and alerts for security and compliance. Yet, despite their value, SIEMs have struggled to keep up with today’s logging performance and scalability requirements. Given that adversaries are operating faster than ever, organizations must prioritize the capabilities that help them identify and respond to threats quickly.
Transforming defence with Elastic AI and data capabilities
How to remove PII from your Elastic data in 3 easy steps
5 Best Practices for Building a Cyber Incident Response Plan
A modern SIEM for whole-of-state cybersecurity
Micro Lesson: Cloud SIEM Outlier Rules
CISOs and cybersecurity in an economic downturn: do more with less
The Future of Cybersecurity: Unleashing the Power of AI and Threat Intelligence
The rapidly evolving landscape of cybersecurity is witnessing the genesis of new paradigms, redefining the ways we perceive threat detection and response. Traditional approaches to cybersecurity are proving less effective against the sophistication of modern cyber threats. Among the many possible solutions, the integration of Threat Intelligence (TI) and Artificial Intelligence (AI) stands as an impressive contender, aiming to set a new standard in the industry.
Container Workload Protection by Elastic
Centralized Log Management for SOX Compliance
Leading the way in the Authentication and Identity category: AD360 wins the Fortress Award 2023
The Business Intelligence Group announced the winners of the Fortress Award 2023 on May 31. We are thrilled to share that ManageEngine AD360 stood out amongst the competition, earning recognition in the Authentication and Identity category. The Fortress Award is a prestigious accolade in the cybersecurity space, and it recognizes outstanding achievements and innovations in the fight against cyberthreats.
Elastic's detection rules are still open for business - plus further visibility to data quality
RCA Series: Root Cause Analysis Overview
Don't let your data rain down: A beginner's guide to cloud security
Supercharge Microsoft Sentinel SIEM with SenseOn
Security information and event management (SIEM) solutions like Microsoft Sentinel SIEM are at the heart of most security operations teams. But like any SIEM, while Microsoft Sentinel can be an incredible tool for centralising security data, it also risks being expensive and ineffective. In a recent webinar I discuss these problems and how SenseOn can help supercharge Azure Sentinel. You can now watch this webinar anytime online.
Improving Cyber Resilience: How Logsign Unified SO Platform Outshines SIEM, SOAR, and XDR
What are the key differences between SIEM, SOAR, XDR & Logsign Unified SO Platform? SIEM, SOAR, XDR and Logsign USO Platform are all cybersecurity technologies that help organizations detect, investigate, and respond to cyber threats. However, they differ in their scope, capabilities, and focus. Here are the key differences between them.
SIEM vs. MSSP vs. MDR: An Essential Guide
SIEM and UEBA: A Match Made in Cybersecurity Heaven
SIEM and UEBA are complementary solutions that can work together to provide a comprehensive view of network activity and enhance the threat detection and response capabilities of cybersecurity teams. By integrating SIEM and UEBA, organizations can benefit from.
Fewer Organizations Outsourcing SOC Activities in 2023
For years, security leaders have debated the advantages of building in-house security operations centers or outsourcing the SOC function to a third party. Both options have their pros and cons. The best choice for each organization depends on a few factors: the type of threats it encounters, the resources it has at its disposal, the complexity and breadth of their attack surface, and the commitment it wants to make to advanced threat hunting.