High-Fidelity Alerts: The Key to Effective API Security
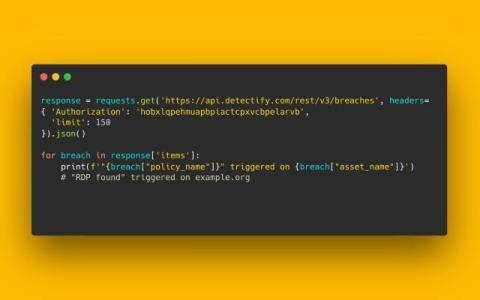
APIs are essential for modern applications as they enable seamless communication and data exchange, serving as the foundation of these applications. However, their interconnected nature makes them vulnerable to various threats. The high volume of API calls - ranging from millions to billions every month - poses a challenge in distinguishing between genuine attacks and harmless irregularities.