Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
January 2024
GitGuardian Honeytoken For Peace Of Mind
Evaluating Secrets Detection Platforms Is Complex: GitGuardian is here to help you navigate the process
Terraform Project for Managing Vault Secrets in a Kubernetes Cluster
What is SCA (Software Composition Analysis) software?
Five Ways Your CI/CD Pipeline Can Be Exploited
Store API keys and other secrets securely in python using env variables
Risks of source code leakage
Has My Secret Leaked? [Security Zines]
What is DAST (Dynamic Application Security Testing) 60 sec explainer
Good Application Security Posture Management Requires Great Data
Discover how GitGuardian enhances Application Security Posture Management, ASPM, with top-notch code security and secrets detection and remediation coordination.
Fast food restaurants hacked simultaneously - Breach breakdown
Three Tips To Use AI Securely at Work
How can developers use AI securely in their tooling and processes, software, and in general? Is AI a friend or foe? Read on to find out.
Understanding the Risks of Long-Lived Kubernetes Service Account Tokens
Kubernetes Service Account tokens are exploited in many attack chain scenarios. Learn how to mitigate these risks and secure your Kubernetes clusters effectively.
What is SAST? Static Application Security Testing explained in 60 seconds
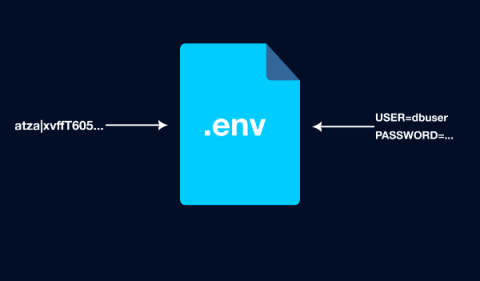
Secure Your Secrets with .env
Using environment variables to store secrets instead of writing them directly into your code is one of the quickest and easiest ways to add a layer of protection to your projects.
Guardian Goofs: Signs Your Developers Are Leaking Secrets
Welcome to 2024 and a new monthly feature here at GitGuardian, a comic strip called "Guardian Goofs." If you like it, please show it some love by hitting one of those "share" links below it. And check back on the first Thursday of each month for the newest "Goof." Share this article on Twitter, HackerNews, LinkedIn, or Reddit.
Application Security Posture Management with GitGuardian and ArmorCode
Managing GitGuardian Findings as Part of a Complete Risk-Based Software Security Program with ArmorCode ASPM.