Prevent Credential Exposure in Code
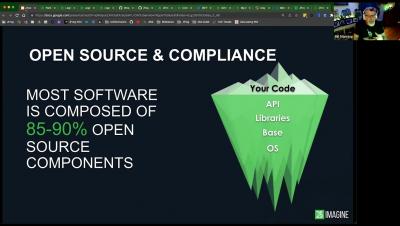
In today’s software development world, developers rely on numerous types of secrets (credentials), to facilitate seamless interaction between application components. As modern applications become more complex and require authentication for services and dependencies, the practice of hardcoding secrets during software development is on the rise.