Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
May 2022
Pyrsia: Decentralized Package Network that Secures the Open Source Supply Chain
Supply chain security has received a lot of attention in recent years. And rightly so. Software vulnerability exploitation attacks have been a key tool in the hands of the hackers to hamper businesses, compromise sensitive data, and a cause of general sense of fear around open source software.
Pyrsia: Open Source Software that Helps Protect the Open Source Supply Chain
Stephen Chin is no stranger to having big ideas and implementing them to help the developer community. In the last twenty years he’s been involved in building open source IDEs, bootstrapping rich client libraries, maintaining JVM languages, and cultivating relationships with developers that do the same.
JFrog Connect: Ready for What's Next for DevSecOps, Edge and IoT
Today at swampUP, our annual DevOps conference, JFrog CTO Yoav Landman unveiled the next step toward making the Liquid Software vision of continuous, secure updates a truly universal reality. We’ve introduced JFrog Connect, a new solution designed to help developers update, manage, monitor, and secure remote Linux & Internet of Things (IoT) devices at scale.
Secure your Software Supply Chain with Xray and Lightstep Incident Response
Securing your software supply chain requires proactively identifying compliance issues and security vulnerabilities early in your software development lifecycle. Additionally early detection must be coupled with an organized and agile method of response that brings together developers, operations and SRE teams to accelerate remediation workflows across the organization.
Automate Security Workflows in ServiceNow with the JFrog Xray Spoke
In 2022, JFrog and ServiceNow engaged in a series of meaningful conversations around the state of DevSecOps and how the industry could benefit from tighter integrations with IT-Operations tools.
npm package hijacking through domain takeover - how bad is this "new" attack?
When relying on a 3rd-party package from a non-commercial entity, there is always the risk of lack of support, especially when it comes to outdated packages and versions. If the package stops being maintained, nobody will implement a new feature we might need or fix a newly-discovered security vulnerability. Consider, for example, CVE-2019-17571. A critical remote code vulnerability which was never fixed in Log4j 1.x, since it was not supported anymore, and only fixed in Log4j 2.x.
DevSecOps 101: Best Practices
JFrog & Industry Leaders Join White House Summit on Open Source Software Security
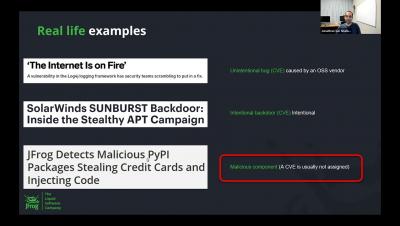
There’s no question the volume, sophistication and severity of software supply chain attacks has increased in the last year. In recent months the JFrog Security Research team tracked nearly 20 different open source software supply chain attacks – two of which were zero day threats.
Scan your software packages for security vulnerabilities with JFrog Xray
Scanning your packages for security vulnerabilities and license violations should be done as early as possible in your SDLC, and the earlier the better. This concept is also known as “Shifting Left”, which helps your organization comply with security policies and standards early on in the software development process. As developers, this may seem like a hassle, but with JFrog CLI it’s easy!
How to Prevent the Next Log4j Style Zero-Day Vulnerability
Software testing is notoriously hard. Search Google for CVEs caused by basic CRLF (newline character) issues and you’ll see thousands of entries. Humanity has been able to put a man on the moon, but it hasn’t yet found a proper way to handle line endings in text files. It’s those subtle corner cases that have a strong tendency of being overlooked by programmers.
OWASP Bay Area Meetup Host Sponsored by JFrog - April 28
(SBOM) Creation of your Software Bill of Materials
npm supply chain attack targets Germany-based companies with dangerous backdoor malware
The JFrog Security research team constantly monitors the npm and PyPI ecosystems for malicious packages that may lead to widespread software supply chain attacks. Last month, we shared a widespread npm attack that targeted users of Azure npm packages. Over the past three weeks, our automated scanners have detected several malicious packages in the npm registry, all using the same payload.
Get Peace of Mind about Security When Deploying Containers from Docker Desktop
Have you ever deployed Docker containers and hoped they delivered safe software? Would you like to get peace of mind that the contents of your containers are secure and clear of vulnerabilities? With JFrog Xray’s new integration with Docker Desktop Extensions, you will be able to do just that. By scanning for vulnerabilities locally before pushing to your remote repositories, your deployed software will inherently be more secure.