Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2023
Lessons from OpenSSL vulnerabilities part 2: Finding and fixing supply chain vulnerabilities
This supply chain series centers on the lessons learned from OpenSSL and what you need to consider when enhancing your supply chain security. While this series will focus on OpenSSL and relevant libraries, we'll also consider vulnerabilities across the board. In the first installment, we covered everything you need to know about where to look for vulnerable libraries.
Preventing Cross-Site Scripting (XSS) in Java applications with Snyk Code
Java is a powerful backend programming language that can also be used to write HTML pages for web applications. However, developers must know the potential security risks associated with Cross-Site Scripting (XSS) attacks when creating these pages. With the rise of modern templating frameworks, preventing security attacks through proper input validation and encoding techniques has become easier.
Best Practices for Your First 30 Days, April 2023
4 best practices for cultivating developer security adoption
Implementing adequate software supply chain security is a challenging feat in 2023. Attackers are becoming more sophisticated, and the growing complexity of modern applications makes them difficult to defend. We’re talking microservices, multi-cloud environments, and complex workflows — all moving at the speed of business. To address these challenges, the Snyk team organized two roundtable discussions, one held in North America and the other in EMEA.
Lessons from OpenSSL vulnerabilities part 1: Preparing your supply chain for the next critical vulnerability
It's early in the morning on an unseasonably warm Tuesday in October. You're checking your email as you enjoy your first cup of coffee or tea for the day, and you almost do a spit-take when you read that OpenSSL has a forthcoming release to fix a CRITICAL vulnerability. Immediately, visions of Heartbleed pop into your head.
Preventing insecure deserialization in Node.js
Serialization is the process of converting a JavaScript object into a stream of sequential bytes to send over a network or save to a database. Serialization changes the original data format while preserving its state and properties, so we can recreate it as needed. With serialization, we can write complex data to files, databases, and inter-process memory — and send that complex data between components and over networks.
Developer-centric DAST with Bright Security
Security testing is increasingly viewed as an essential part of the software development lifecycle (SDLC). Traditionally, agile software development has focused on development velocity, rapid market feedback, and delivering high quality products and services. However, software that's vulnerable to cyber attacks is not valuable to end users and creates huge risks for both customers and software vendors. This makes it critical to integrate security testing into the software development process.
The importance of platform engineers in a security program
Platform engineers need to be empowered in an organization’s security program. Their work has huge leverage over a product's security posture, arguably as great an impact (some would even say greater) than application vulnerabilities. Despite the significance of the impact of their work, their role in security programs remain ill-defined.
Identify vulnerabilities in your container images with Snyk's enhanced Docker Desktop Extension
The Docker developer ecosystem is continuously growing, and container security is becoming even more important as the Docker developer ecosystem evolves. The developer-friendly Snyk security integration with Docker is invaluable in today’s landscape. Snyk has made significant updates to the Docker Desktop Extension and continues to evolve the extension to ensure the applications and images pushed to the container registry don't have critical vulnerabilities.
5 ways to improve security during digital transformation
Digital transformation initiatives have pushed software development to the next level. Today's consumers demand an optimum customer experience and expect modern apps to live up to high expectations. So, the average developer in 2023 must keep up with faster delivery, more eye-catching features, and better functionality. This unprecedented growth in the software development industry has led to a massive disparity between development and security teams.
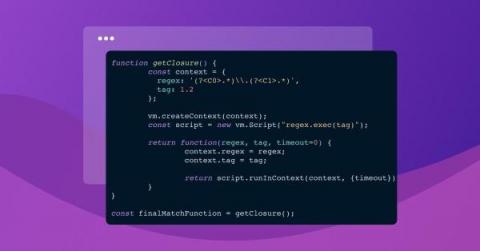
Timing out synchronous functions with regex
How hard can it be to support custom container image tags? Turns out… quite! I know this because my team has been busy at work on our new custom base image support for Snyk Container, andwe were tasked with the following problem: Given a tag, parse its parts to be able to compare it to other similar tags. It was a fun problem to solve, and we'd love to share how we got to our final solution!
SnykLaunch recap: Custom Base Image Recommendations
One of the exciting new features discussed at SnykLaunch today was Custom Base Image Recommendations (CBIR). In open beta since late 2022, CBIR is already being used by several organizations. We've been expanding the feature set as we approach general availability to include more flexibility and to incorporate hands-off automation capabilities, allowing users to leverage CBIR in their CI/CD pipelines.
SnykLaunch April '23: C/C++ expansion, cloud and IaC updates, custom container security, new integrations, and more
This month, we hosted our most recent SnykLaunch to announce the latest and greatest in Snyk solutions. As with all of our releases, we continue to focus on adapting security to what we see in modern-day development practices. Compared to only a few years ago, more independent development teams are working faster, along with a far more complex software supply chain, including cloud as part of the code. Because development practices look so different today, security teams often struggle to keep up.
Snyk brings developer-first AppSec approach to C/C++
Snyk is known for its developer-first application security solutions for many ecosystems like Java, JavaScript, Python, and more. Snyk enables developers to not only find issues but quickly apply fixes, revolutionizing security and supporting its integration at the earliest stages of the SDLC. In 2022, we released the first round of support for C/C++ open source packages, and today we’re excited to announce the Open Beta of C/C++ for Snyk Code and licenses for Snyk Open Source.
Fix cloud security issues faster and at the source with Snyk Cloud
In July 2022, we announced Snyk Cloud, extending the Snyk developer security platform to secure application and infrastructure configurations in running cloud environments. Today, we’re thrilled to introduce a new feature of Snyk Cloud that enables you to "fix cloud issues in IaC" (infrastructure as code), making Snyk Cloud the first solution to secure the cloud through code with remediation paths in IaC.
How Snyk uses AI in developer security
As a leader in applying AI to developer security, Snyk’s approach is unique. Today, we want to provide a glimpse at how Snyk currently uses AI and data science, as well as a sneak peek at what’s to come. Before diving in, we want to highlight two aspects of Snyk’s use of AI to set the stage.
Snyk achieves Red Hat Vulnerability Scanner Certification
We are thrilled to announce that Snyk has achieved Red Hat Vulnerability Scanner Certification, making it one of the few security platforms to receive this certification from Red Hat. This achievement demonstrates Snyk’s ongoing commitment to providing our customers with the highest level of security assurance for their applications.
Recap: Stress-Free Security for Devs and Ops on AWS
Snyk recently hosted a half-day virtual event focused on security for application workloads running on AWS (you can catch it on demand here). The event was broken into six sessions spanning topics like developer challenges in cloud-native AppDev, top vulnerabilities from last year, hands-on workshops with industry-leading technology vendors, and several other subjects that help enable engineering and security teams to build a successful DevSecOps workflow.
The Snyk Perpetual Key Rotation Machine
At Snyk, we think of developers as citizens of a special community. In that community, your collection of apps is your neighborhood — and your code is your home base; your house. How do you secure a house? With a lock! And how do you make sure no one else can unlock that lock? You keep the key! That’s security ideation at its finest: keys. Just ask Vinz Clortho, Keymaster of Gozer.