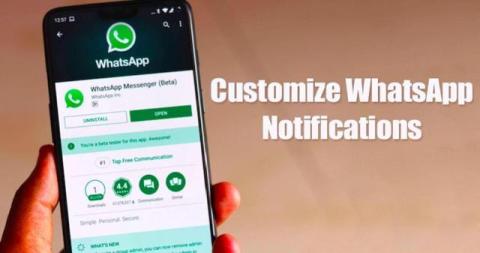
How can WhatsApp users customize notifications for improved privacy?
Have you ever felt like your WhatsApp notifications are telling everyone about your business? Don't worry! There are ways to make your messages more private. WhatsApp offers various customization options to improve your privacy and minimize distractions.