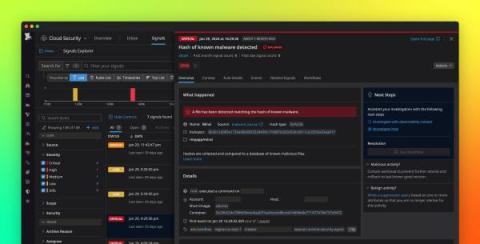
Detect malware in your containers with Datadog Cloud Security Management
Detecting malware in container environments can be a major challenge due to the rapid development of malicious code, the proliferation of insecure container images, and the multilayered complexity of container stacks. Staying ahead of attackers means tracking the constant evolution of malware and rooting out threats in your codebase at the expense of considerable compute.