Tenable for Vulnerability Scans: Maximizing Your Security Posture
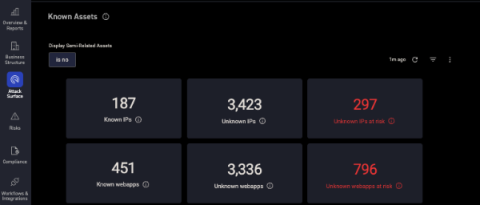
Vulnerability scans are essential to an effective cyber defense strategy, offering a proactive approach to uncover and mitigate potential threats before they can exploit your systems. At the forefront of this crucial practice are Tenable and RiskOptics, each offering comprehensive solutions designed to conduct thorough vulnerability assessments. These tools identify weaknesses and help prioritize and address them, significantly strengthening your overall security posture.