Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
Predictive Vulnerability Management: Operationalizing EPSS with Business Context
Join us for an in-depth webinar on the Exploit Prediction Scoring System (EPSS), a powerful tool for predicting the exploitability of vulnerabilities. This discussion features experts Jay Jacobs from Cyentia and Stephen Schafferr from Peloton Interactive. They explore the intricacies of EPSS, its application, and the benefits of using EPSS over traditional methods like CVSS for better vulnerability management. Key topics include operationalizing EPSS, leveraging threat intelligence, and creating effective prioritization strategies. .
Agent hijacking: The true impact of prompt injection attacks
Over the last 18 months, you’ve probably heard about Large Language Models (LLMs) like OpenAI’s GPT and Google’s Gemini. Whether you’re using them as a personal research assistant, an editor, or a data analyst, these tools represent a new frontier of Machine Learning (ML) and Artificial Intelligence (AI) and arguably will have the most significant impact of any technology in this decade.
Network Vulnerabilities and Threats: A Cyber-Security Challenge
The digital world is under constant risk as cyber-attacks are becoming increasingly advanced and increasing at a staggering rate. While significant developments have been made to mitigate cyber risk, network security threats continue to evolve further to get unauthorized access and steal data from companies. According to Cloudwards Cybersecurity Statistics 2024, Cybersecurity intrusions increased by 613% from 2013 to 2023.
CVE-2024-40766: Critical Improper Access Control Vulnerability Impacting SonicOS
On August 22, 2024, SonicWall published a security advisory regarding a critical improper access control vulnerability in several SonicWall Firewall models. This vulnerability, identified as CVE-2024-40766, is a flaw in SonicOS, the operating system that powers these firewalls. CVE-2024-40766 allows a remote, unauthenticated attacker to gain unauthorized access to resources and/or cause the firewall to crash under specific conditions.
Snyk Code, the only security tool chosen by developers in Stack Overflow's 2024 AI Search and Developer Tools survey
Snyk Code was the only code security tool shortlisted by developers as an AI tool they’ve been regularly using this past year or are looking forward to using next year in Stack Overflow’s recent 2024 AI Search and Developer Tools survey. This underlines Snyk’s dominance as the favorite AI security tool of both developers and security teams and confirms that Snyk Code is providing immense value to developers.
Windows Downdate Attacks, Quick Share Vulnerability Exploit, and More: Hacker's Playbook Threat Coverage Round-up: August 2024
In this version of the Hacker’s Playbook Threat Coverage round-up, we are highlighting attack coverage for several new threats, including those discovered via original research by the SafeBreach Labs team. SafeBreach customers can select and run these attacks and more from the SafeBreach Hacker’s Playbook to ensure coverage against these advanced threats. Additional details about the threats and our coverage can be seen below.
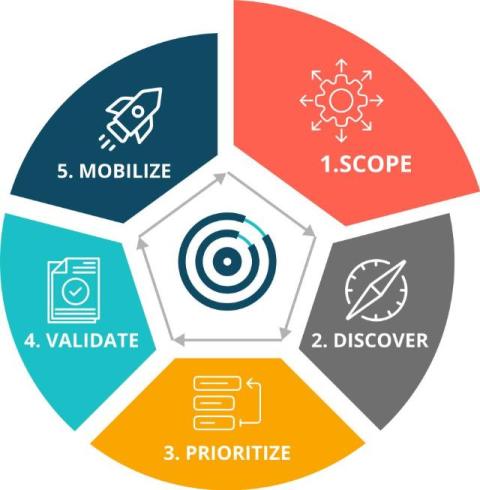
CTEM step-by-step guide | Stage one: Scoping
Welcome to our blog series on Continuous Threat Exposure Management (CTEM), where we dig into the five essential stages of implementing a robust CTEM program. Coined by Gartner in 2022, CTEM is a powerful process that can help continuously manage cyber hygiene and risk across your online environment. It’s also a lot to think about when you’re starting out, so it helps to break things down. Our series begins with the crucial first stage: Scoping.
ARMO's new security-boosting summer cocktail: Layered Vulnerability Scanning, SBOM View, and new Auto-Generated Network Policies
This summer ARMO is proud to announce a batch of new features designed to enhance your cloud security posture. We developed groundbreaking capabilities for in-depth vulnerability scanning, simplified vulnerability management with SBOM view, and streamlined network policy generation for two popular CNIs, Calico and Cilium.. We invite you to explore these new features and discover how they can add to your organization’s security. Let’s go.