Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
AI Hallucinations and Manipulation: AI Code Vulnerabilities in React and Fastify Node.js (part 2)
How to Streamline Vulnerability Management
The current cyber world is a veritable minefield, with problems and dangers evolving at a rate that far outstrips the ability of most organizations to respond. More than merely a technical issue, an organization's security posture is determined by the quality of its vulnerability management.
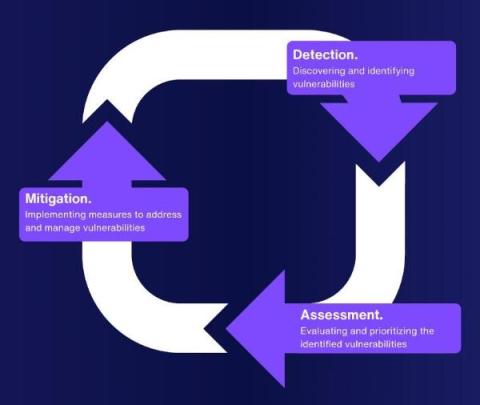
Job-to-be-Done: Quickly resolve exposures and vulnerabilities
It’s not unlikely that your team has a sufficient amount of vulnerability data that they must assess, prioritize, and remediate. Whether that’s a newly discovered vulnerability, an expired SSL certificate, or even a security policy breach – security teams need to get all this data into one place. For AppSec and ProdSec teams to be successful, they need to know which of their assets are exposed and vulnerable so they can take action to enable faster remediation.
CVE-2023-46747: Critical Unauthenticated RCE Vulnerability in F5 BIG-IP
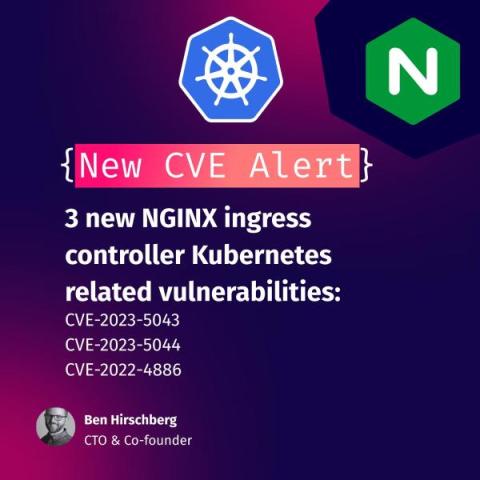
Three new NGINX ingress controller vulnerabilities reported and how they affect Kubernetes
DC Board of Elections breach: Voter data is now online and up for sale
Earlier this month, the District of Columbia Board of Elections (DCBOE) warned that a threat actor may have gained access to the personal information of their registered voters. This would include personally identifiable information (PII) such as contact details, partial social security numbers, dates of birth, and driver’s license numbers. In an X post on Friday 20th October, the agency was keen to stress that it was only a possibility the voter roll had been accessed.
Fireblocks researchers uncover first Account Abstraction wallet vulnerability
The Fireblocks research team recently uncovered an ERC-4337 Account Abstraction vulnerability in the smart contract wallet UniPass. Fireblocks worked with UniPass to fully mitigate the vulnerability, which was found in hundreds of mainnet wallets in a whitehat operation. All funds are now safe and accounted for.