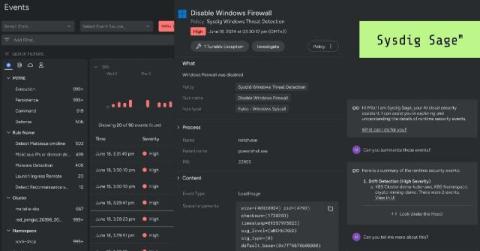
LLM Security: Splunk & OWASP Top 10 for LLM-based Applications
As a small kid, I remember watching flying monkeys, talking lions, and houses landing on evil witches in the film The Wizard of Oz and thinking how amazing it was. Once the curtain pulled back, exposing the wizard as a smart but ordinary person, I felt slightly let down. The recent explosion of AI, and more specifically, large language models (LLMs), feels similar. On the surface, they look like magic, but behind the curtain, LLMs are just complex systems created by humans.