Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Uncovering the powers of Cloud SOAR's Open Integration Framework
ImmuniWeb Named to 2021 AIFinTech100 List
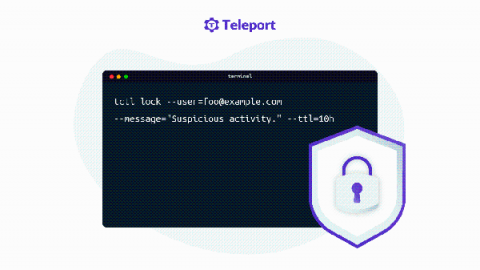
Security Incident Containment with Teleport Session and Identity Locking
What would you do when a security incident is detected? Shut down the servers? Pull out the power cord from the data center? When an incident is detected, both the incident method and the time required to contain an incident are essential to limit the damage. The slower you are to react, the more damage an incident would incur. And a service downtime to contain an incident can cost businesses even more than a security incident itself.
Clearing Up Elements of Cloud Security | Ep 24
Strengthen your cloud security posture with Azure Sentinel
Scalable, cloud-native solutions like Azure Sentinel help security teams streamline security operations in cloud environments. In this first of a two-part blog series, we explore the challenges businesses face when detecting and responding to cyber threats and attacks, and how these challenges can be addressed by leveraging Microsoft Azure Sentinel.
Understanding Security Service Edge (SSE) and SASE
The SASE journey requires reliable partners with truly integrated platform capabilities, not vendors wielding smoke-and-mirrors-style marketing proclaiming “SASE” in giant headlines. But clarity is critical, and both SASE and the more-recently-coined security service edge (SSE) terminology, can be a little confusing.
Hacker School Reboot - insights from leading API hackers [VIDEO]
Detectify is on a mission to drive the future of Internet security with automated and crowdsourced web solutions. API security and hacking is a pretty hot topic today and we invite 3 experts to join us for the latest Detectify Hacker School Reboot to present lightning talks on their experience and interests in hacking APIs. Detectify recently announced that we are researching, breaking and securing APIs.
The biggest threat to modern society - and its not Covid
5G robots began their first scouts around Singapore’s luxury neighbourhood Keppel Bay last month - a trend that will spread globally in the years to come. These autonomous robots came in several forms, and were adapted specifically for a variety of duties that gave ground staff a chance to perform their duties via proxy, away from the hot tropical sun. This included monitoring water quality, garbage collection, and security surveillance.
Open Source Risk Management in the Financial Sector
Banking has changed. In the past, financial institutions outsourced their technology. They had large consulting firms creating, managing, and maintaining their back-end systems. Although banks would have knowledge of the systems in place, they wouldn’t be running them on a day-to-day basis. That was the consultants’ responsibility. Recent years have seen a significant shift in the financial sector.