Protecting Cloud Workloads with CrowdStrike and AWS
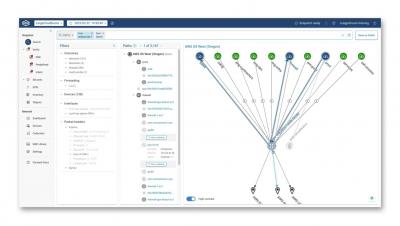
Migrating to the cloud has allowed many organizations to reduce costs, innovate faster and deliver business results more effectively. However, as businesses expand their cloud investments, they must adapt their security strategies to stay one step ahead of threats that target their expanded environment. Managing, securing and having visibility across endpoints, networks and workloads is not an easy feat. It requires a unified defense-in-depth approach.