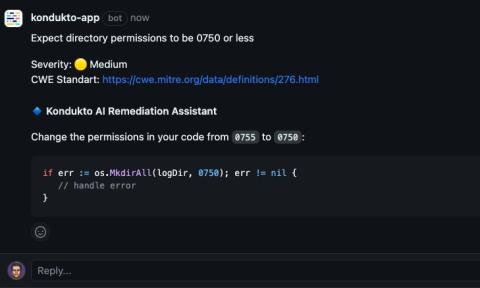
AI Remediation: A massive time-saver
One of the biggest challenges that application security engineers are facing is the large amount of false positives from security scanners. False positives are results that indicate a vulnerability where there is none, or where the risk is negligible. Triaging these false positives wastes a lot of time.