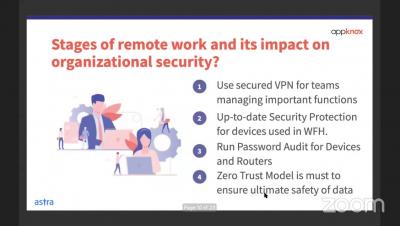
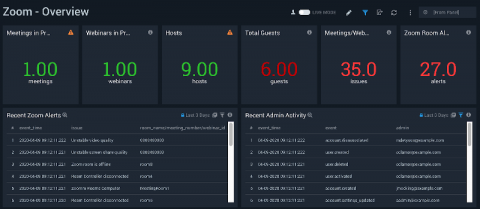
Pros and Cons of the FAIR Framework
The Factor Analysis of Information Risk (FAIR) framework was developed by Jack Jones. FAIR is a risk management framework championed by the open group that enables organizations to analyze, measure, and understand risk. The FAIR model evaluates factors that contribute to IT risk and how they impact each other while breaking down risk by identifying and defining the risk model. FAIR is most often used to establish probabilities for the frequency and magnitude of data loss.