Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
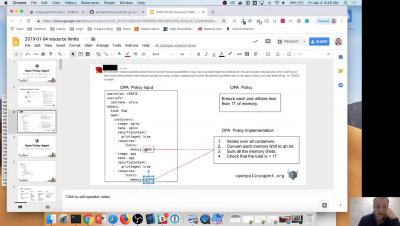
OPA policy for Kubernetes label management
Ignyte Governance, Risk, and Compliance
Adding CVE scanning to a CI/CD pipeline
A Docker image contains an application and all its dependencies. As it also contains the numerous binaries and libraries of an OS, it’s important to make sure no vulnerabilities exist in its root filesystem, or at least no critical or major ones. Scanning an image within a CI/CD pipeline can ensure this additional level of security.
Fight Timecard Fraud and Wage Theft with Employee Monitoring
One type of employee fraud is timecard fraud. No matter the size of your organization, having dedicated, hard-working employees is essential to your bottom line, reputation and business goals.
What You Need to Know About Secure Mobile Messaging in Healthcare
With the majority of people using smartphones these days, texting is all but a given when trying to communicate with your friends or family. But what about your doctor? A recent study determined that 96 percent of physicians use text messaging for coordinating patient care. This can raise eyebrows and red flags.
Weekly Cyber Security News 11/01/19
A selection of this week’s more interesting vulnerability disclosures and cyber security news. Another week in to 2019 and it’s just not getting better is it? Some more pretty big breaches and the worst; companies that should know better apparently missing the mark.
Top 12 Blogs of 2018
Time to look back on the top AlienVault blogs of 2018! Here we go...
Detectify security updates for 10 January
For continuous coverage, we push out major Detectify security updates every two weeks, keeping our tool up-to-date with new findings, features and improvements sourced from our security researchers and Crowdsource ethical hacker community. Due to confidentially agreements, we cannot publicize all security update releases here but they are immediately added to our scanner and available to all users. This post highlights a few things that we have improved in the last two weeks.
What is server side request forgery (SSRF)?
Server Side Request Forgery (SSRF) is a type of attack that can be carried out to compromise a server. The exploitation of a SSRF vulnerability enables attackers to send requests made by the web application, often targeting internal systems behind a firewall.