How to implement guardrails for AWS EKS
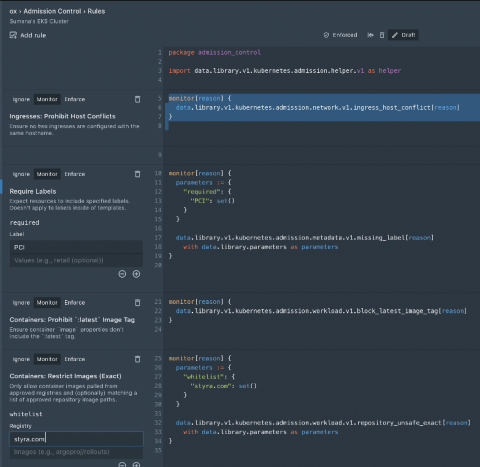
Today marked the first ever AWS re:Inforce security conference, and Styra was well represented. Paavan Mistry from AWS took the stage to walk through an EKS Security session with Synamedia, wherein they talked about the great responsibility organizations have over their Kubernetes environments.