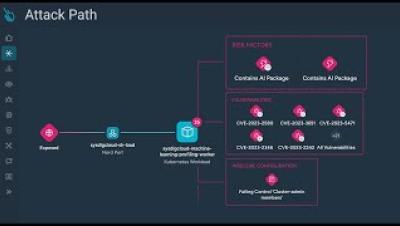
New Research Finds Phishing Scams Targeting Popular PDF Viewer
Several phishing campaigns are targeting users of the Foxit PDF Reader, according to researchers at Check Point. Foxit is a popular alternative to Adobe Acrobat Reader for viewing PDF files. “Check Point Research has identified an unusual pattern of behavior involving PDF exploitation, mainly targeting users of Foxit Reader,” the researchers write. “This exploit triggers security warnings that could deceive unsuspecting users into executing harmful commands.