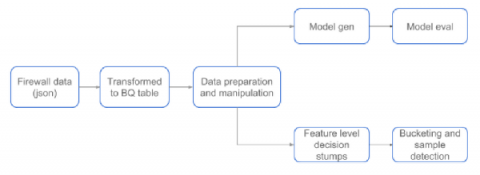
Forseti intelligent agents: an open-source anomaly detection module
Among security professionals, one way to identify a breach or spurious entity is to detect anomalies and abnormalities in customer’ usage trend. At Google, we use Forseti, a community-driven collection of open-source tools to improve the security of Google Cloud Platform (GCP) environments. Recently, we launched the “Forseti Intelligent Agents” initiative to identify anomalies, enable systems to take advantage of common user usage patterns, and identify other outlier data points.