Approaching Kubernetes Security - Detecting Kubernetes Scan with Splunk
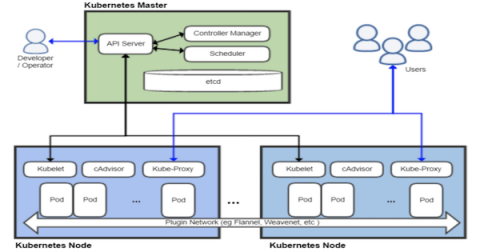
The Kubernetes framework has become the leading orchestration platform. Originally developed by Google, Kubernetes is a "platform for automating deployment, scaling, and operations of application containers across clusters of hosts" * . The kubernetes platform is used in all Cloud platform provider vendors as a tool that allows orchestration, automation and provision of applications and specific needs computing clusters and services.