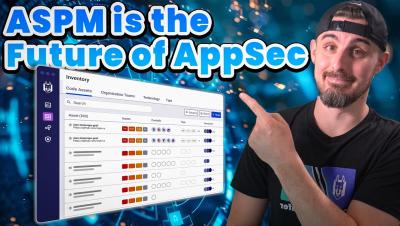
GitGuardian SCA Makes It Easy To Manage SBOMs
GitGuardian SCA makes it easier than ever to build and group your SBOMs while staying up to date with any changes. Our Software Composition Analysis tool, better known as GitGuardian SCA, lets you instantly download up-to-date Software Bills of Material with the touch of a button. No more guessing if things have changed between the last version someone else generated and now. You'll never need to ask your developers to generate a fresh SBOM again.