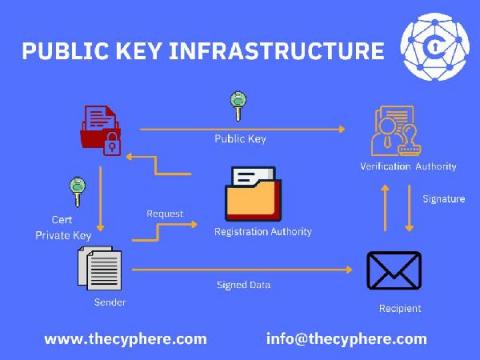
Creating a custom Temporal data convertor for encryption
Nightfall is a data security vendor that integrates with our customers’ third party applications (Slack, Google Drive, Github, Jira etc) to, on a continuous real-time basis, scan all content being added to these applications for sensitive data.