Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Encryption
What is Encryption? How It Works and Its Benefits
Encryption technology is vital to securely sharing information over the internet. An estimated 1.145 trillion MB of data is created every day, and encryption prevents sensitive information from being intercepted, read or altered by the wrong recipients. Not sure what encryption is or how it works? Keep reading to learn more about data encryption, its purpose and benefits.
Symmetric Encryption vs. Asymmetric Encryption? How it Works and Why it's Used
Cybersecurity is a top priority for businesses, governments, and individuals alike. With the rise of cybercrime in recent years, it’s more important than ever to ensure that sensitive data is kept safe and secure. That’s where encryption comes in. Encryption is the process of encoding data so that only authorized users can access it. There are two main types of encryption: symmetric and asymmetric encryption.
OWASP Top 10: Cryptographic failures
Cryptography 101: Key Principles, Major Types, Use Cases & Algorithms
How End-to-End Encryption in Messaging Apps Benefits Your Business
Improve your AWS security posture, Step 3: Encrypt AWS data in transit and at rest
In the first two blogs in this series, we discussed properly setting up IAM and avoiding direct internet access to AWS resources. In this blog, we’ll tackle encrypting AWS in transit and at rest.
What is a Cipher Suite?
How SSL Encryption and SSL Decryption Work
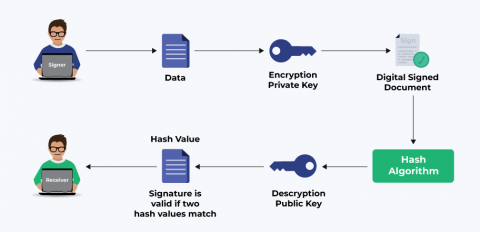
What are the Differences Between Encryption and Signing? Why Should You Use Digital Signatures?
While we have all used digital security certificates like SSL/TLS, code signing certificates, or others, many don’t know the security technology behind them. Stringent security standards ensure that the cyber threats looming around us never get to our digital systems. Due to such threats, there’s a constant advancement happening in data security technology to protect sensitive information. Encryption and Signing are two methods used widely for data security.