How to Manage Technological Risks?
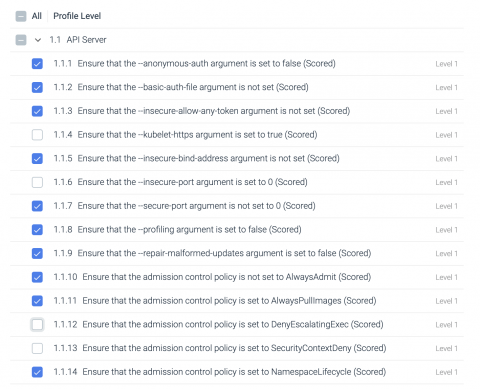
In all sectors, technology has become a vital aspect of operations and has transformed the workplace, but that dependence on technologies also poses a threat to organizational wellbeing. Data breaches, system failures, malicious attacks–as well as natural disasters that impact technologies–can wreak havoc on company reputations, regulatory compliance and fiscal health.