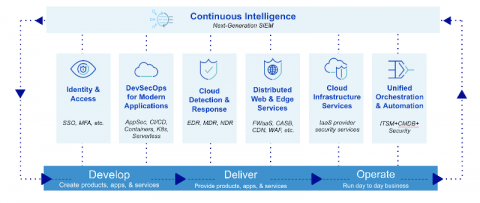
Achieving Compliance with Qatar's National Information Assurance Policy
Qatar is one of the wealthiest countries in the world. Finances Online, Global Finance Magazine and others consider it to be the wealthiest nation. This is because the country has a small population of under 3 million but relies on oil for the majority of its exports and Gross Domestic Product (GDP). These two factors helped to push the country’s GDP measured at purchasing power parity (PPP) to over 132,886, per Global Finance Magazine’s findings in August 2020.