Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Java
What you need to know about Log4Shell
Photo by ThisIsEngineering from Pexels Considered one of the largest exploitable vulnerabilities in history, Log4Shell affects many as Log4J is one of the most extensively used logging libraries. An issue that has existed for almost a decade but just recently was discovered, Log4Shell leaves companies vulnerable to the full extent of these attacks. AT&T Alien Labs blogged about the vulnerability back in December 2021, with more technical detail.
Log4Shell Peace of Mind in Minutes, Not Weeks
Discovered on December 9, 2021, the log4Shell vulnerability is one of the most talked-about vulnerabilities in computing. Because simple text can be used to take control of a device and download anything that is Internet-accessible, companies are taking it seriously. As they should – log4Shell has the maximum CVSS score of 10 (CVSS, Common Vulnerability Scoring System, is an industry-standard for ranking vulnerabilities).
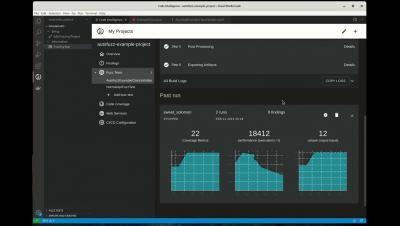
Log4Shell remediation with Snyk by the numbers
We’re almost two months from the disclosure of Log4Shell, and we here at Snyk couldn’t be more excited with the role we’ve gotten to play in finding and fixing this critical vulnerability that’s impacted so many Java shops. For starters, we’ve been able to help our customers remediate Log4Shell 100x faster than the industry average! How have we been able to achieve that?
Log4Shell Live Hack: A Hands-on, Actionable Fix Guide
Log4j Update: Brian Roche - Chief Product Officer
Log4Shell in the Field - A Brief Analysis Through January 2022
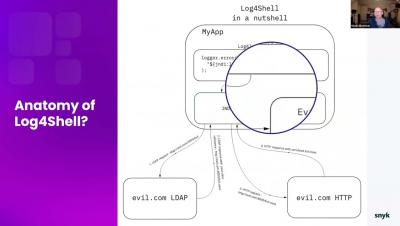
Stranger Danger: Live hack of how a Log4Shell exploit works
The Log4Shell vulnerability took the Java community by surprise at the end of 2021, and many organizations are still mitigating its impact. To help development teams stay informed as the situation unfolds, Snyk has created and continues to update its Log4j vulnerability resource center.
How To Detect & Mitigate Apache Log4j CVE-2021-44228
If you've already heard about the Apache Log4j CVE-2021-44228 (also known as Log4Shell and formally LogJam) vulnerability then you will know that this is a significant issue as many organisations are scrambling to secure their infrastructure from this critical remote code execution (RCE) vulnerability. With these considerations in mind, we wanted to bring you a guide that outlines the steps that can be followed to ensure the security of your systems from CVE-2021-44228.