Role of Identity and Access Management in Cybersecurity
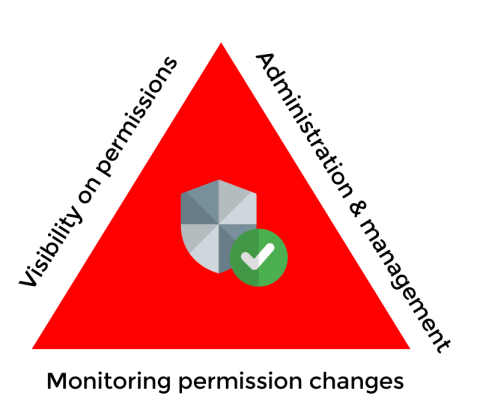
In IT security debates, projects aimed at managing access and identifying users are considered fundamental. However, the processes and technologies for controlling permissions have proved challenging. To solve this dilemma, what is now called Identity Access Management (IAM) was created, which involves the definition and execution of identification processes related to the most critical businesses for a company.