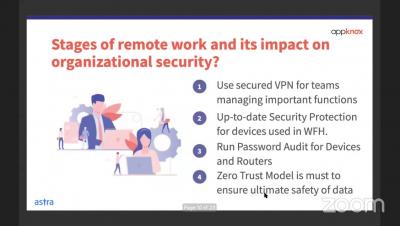
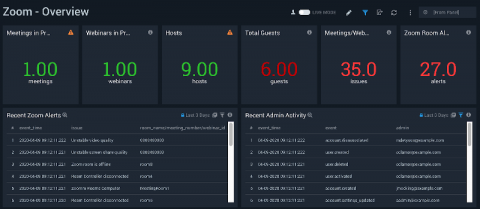
Threat Modeling in Times of Crisis
With most of the country sheltering in place and so many people working remotely, work-life balance is taking on a new meaning and cloud infrastructure is taking a beating. The dramatic increase in daily activity and network use is creating both a visibility challenge and an operating model shift for already lean security teams.