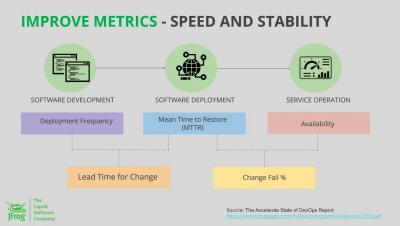
The Importance of User Behavior Analytics
There’s no question that cybercrimes are a growing problem for businesses in the United States. A cyberattack can cost a business about $200,000 on average. Sadly, many businesses that are targeted cannot recover from the financial effects of a cyberattack. In fact, it’s estimated that 60% of targeted companies go out of business within six months of the attack.