Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
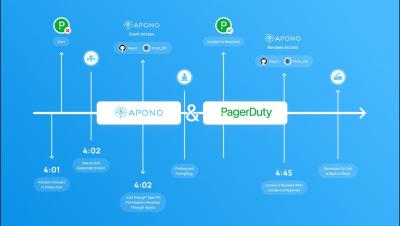
Incident Management
The SEC demands more transparency about Cybersecurity incidents in public companies
The Securities and Exchange Commission (SEC) has introduced a new rule for public companies that requires them to be more transparent about cybersecurity incidents. The new rule requires companies to disclose any material cybersecurity incidents within four business days of that determination. The disclosure should describe the material aspects of the incident, including the nature of the incident, the impact on the company, and the company's response.
Transforming Security and Access with BoxyHQ's SSO Solution - A Conversation with the Spike Team
Spike is a powerful incident management platform with customers across 40+ countries. Their mission is to reduce the complexity of managing incidents and make it simple so teams of all sizes can use it.
9 Common Types of Security Incidents and How to Handle Them
Fitting incident management into the SOC 2 puzzle
In today’s business landscape, security and compliance mean everything. Because of this, many modern businesses look towards solutions that will provide customers and prospects with the most confidence and trust. One of these is SOC 2 compliance and attestation. SOC 2 is a marker of solid and consumer-minded companies that want to protect customer data.
Differentiate your business and accelerate growth with Total Experience (TX) for ServiceNow
For a competitive advantage, transform agent, customer, and employee experiences with proactive incident management via self-service software management and real-time incident remediation.
Cloud forensics - An introduction to investigating security incidents in AWS, Azure and GCP
The cloud has revolutionized the way we do business. It has made it possible for us to store and access data from anywhere in the world, and it has also made it possible for us to scale our businesses up or down as needed. However, the cloud also brings with it new challenges. One of the biggest challenges is just keeping track of all of the data that is stored in the cloud. This can make it difficult to identify and respond to security incidents.
GitGuardian Playbooks - Auto-Granting Access To Incidents
Remediating Incidents With The GitGuardian API [cheat sheet included]
The GitGuardian API lets you remediate your secret incidents from any platform you prefer. We are proud to release a new demo application to help you learn how to automate your workflows.