Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
A Sub-Domain Takeover Story, Two Questions for Every WAF Provider | Sunil Agrawal (CISO, Glean)
Going Beyond Network Perimeter Security by Adopting Device Trust
It’s a familiar nightmare you’ve heard of and might even face as a developer or security engineer: alerts firing in all directions warning that your company’s VPN and firewall — that supposedly “safe” defensive perimeter around your infrastructure — has been breached. And the scariest part is that you find out after the fact — after access credentials and customer assets have been stolen.
Asset Visibility and Behavior: The Keys to Segmentation Success
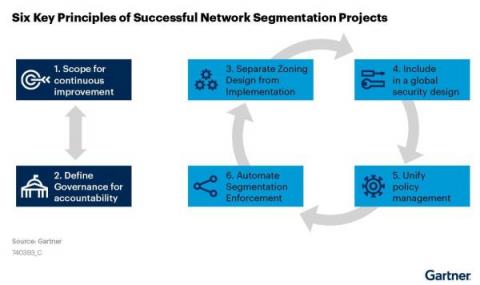
Recently, Gartner® refreshed one of its foundational cybersecurity research, “The 6 Principles of Successful Network Segmentation Strategies.”1 The principles covered in the research are tried and true. Segmenting networks to improve security and performance is nothing new to security teams, yet the same challenges persist year after year.
Need to Improve Efficiency? Access the Data in Your Network for Better Performance, Security, and Reliability
TLDR – watch our presentation on the Tech Field Day YouTube Channel. How many times have you been asked to improve efficiency, do more with less, or work with fewer staff than needed due to talent shortages or resource constraints? Throughout my decades-long IT career, the network has been the backbone of the business – yet our teams are always expected to do more with less and to be bulletproof while we’re doing it. And somehow, we always rise to the challenge.
Report: 78% of channel partners have "more to do" in shift to services and subscriptions
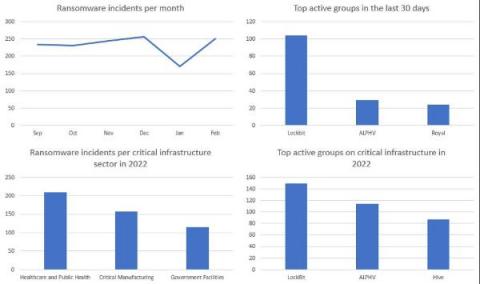
Detect the Most Common Ransomware TTPs to Prevent Attacks
In our new threat briefing, Forescout’s Vedere Labs details tactics, techniques and procedures (TTPs) commonly adopted by ransomware groups and provides specific mitigation recommendations. In addition to basic cyber hygiene practices, we recommend using Forescout XDR for extended detection and response. Its 1,500+ detection rules cover hundreds of the TTPs most commonly used by ransomware.
Merging WAF and IAM Capabilities for Next-gen Security | Scott Tomilson (Sr.Director, Ping Identity)
Are You Trapped in the Upside-Down World of Networking and Security?
Many enterprises today are exploring the benefits of Secure Access Service Edge (SASE). SASE is a modern networking and security solution for enterprises that converges SD-WAN and network security solutions like NGFW, IPS, and NGAM. SASE provides a single, unified and cloud-native network and security service that is adapted to current and future technology and business needs.