Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Top Reasons to Choose Spambrella when relying on Office 365 security
Organizations Using Office 365 Are Choosing Spambrella For The Following Reasons...
Sales Play Book - Value Proposition
Today’s email attacks (ransomware, business email compromise, and sandbox evasion) have evolved, and are outpacing the tools developed to combat them. While they may help with some aspects of email security or stop some attacks, they don’t solve the whole problem and attacks need only succeed once to seriously harm people, data, and brands. Partial security is not security.
Observability and Visibility in DevSecOps
Companies often turn to software as a solution when they need to solve a problem. Whether it’s to automate or enhance a task, or gain valuable information in an easily consumable fashion. The same is true for security teams on both sides of the red and blue line. Security professionals build tools to automate exploitation, detect attacks, or process large amounts of data into a usable form.
Building and Evaluating a Threat Intelligence Program (Part 2)
In the second part, we will take the discussion forward from where we left in the first part. Earlier, we have discussed the basics of threat intelligence and its types. In this post, we will discuss various considerations while building a threat intelligence plan.
Why Your SOC Needs More Than a SIEM Tool
Cybercrime is becoming more sophisticated by the day. Meanwhile, the price for a breach due to damage and disruption, ransom payments and regulatory fines, is increasing. No wonder there’s more of a need than ever for companies to set up a dedicated SOC using SIEM to identify threats and raise the alarm. But is that enough to fight the hackers?
Exposing the common flaws penetration testers always see
We live in an age where cyber security threats are (or at least should be) at the forefront of everyone’s mind. Very recently, British Airways suffered a huge security breach that led to over 300,000 payment cards being compromised, showing that even the big players can still get hacked if they’re not 100% vigilant.
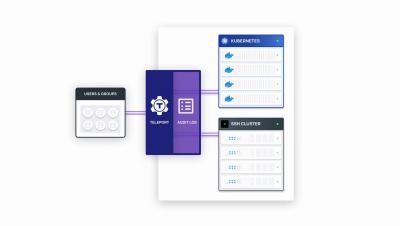
Teleport 3.0 Demo
Using Devo Panels
Encryption by Boxcryptor - Strong Security for the Cloud
The cloud enables teams to collaborate on shared files from anywhere in the world. Whether hosted internally or through a third-party provider, the cloud may very well be one of the biggest collaborative resources to date. Unfortunately, greater accessibility means an increased risk of data loss or theft. For some enterprises, this is a worst-case scenario.