Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
Securing your SaaS apps in 2020: 3 pillars you can't neglect
Using Auditbeat to protect your critical infrastructure
Beats are lightweight, purpose-built agents that acquire data and then feed it to Elasticsearch. Beats use the libbeat framework that makes it easy to create customized beats for any type of data you’d like to send to Elasticsearch. Auditbeat is a lightweight shipper from the Beats family that you can install on your servers to audit the activities of users and processes on your systems.
Announcing the latest version of Security Monitoring for Splunk App
It’s been a while since I have had the pleasure of announcing a new version of Security Monitoring (September 2018), but today I am doing just that. There is nothing better to inspire spending your evenings coding and playing with Splunk than your partner watching shows that just don’t interest you! For my UK friends, yes ‘Love Island’ is that show and for my more international friends "look it up!". So, what updates did I bring?
The total business impact of Sumo Logic Cloud SIEM
Elastic SIEM for home and small business: Beats on Mac
Hey, there. This is part six of the Elastic SIEM for home and small business blog series. If you haven’t read the first, second, and third blogs, you may want to before going any further. In the Getting started blog, we created our Elasticsearch Service deployment and started collecting data from one of our computers using Winlogbeat. In the Securing cluster access blog, we secured access to our cluster by restricting privileges for users and Beats.
Detecting CVE-2020-0601 Exploitation Attempts With Wire & Log Data
Editor’s note: CVE-2020-0601, unsurprisingly, has created a great deal of interest and concern. There is so much going on that we could not adequately provide a full accounting in a single blog post! This post focuses on detection of the vulnerability based on network logs, specifically Zeek as well as Endpoint. If you are collecting vulnerability scan data and need to keep an eye on your inventory of systems that are at risk, then check out Anthony Perez’s blog.
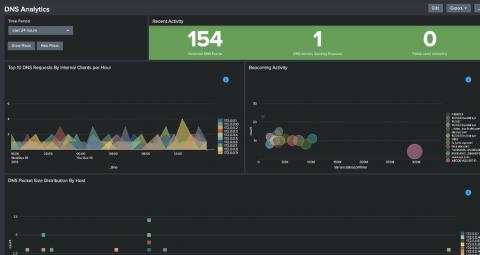
10 Alerts and Visualizations for S3 Server Access Logs to take control of AWS infrastructure
AWS S3 Server Access logs provide detailed records for requests made to S3 buckets. They’re useful for many applications. For example, access log information can be useful in security and access audits. It can also help generate customer insights and better understand your Amazon S3 bill. Coralogix makes it easy to integrate with your S3 server access logs via a Lambda function.
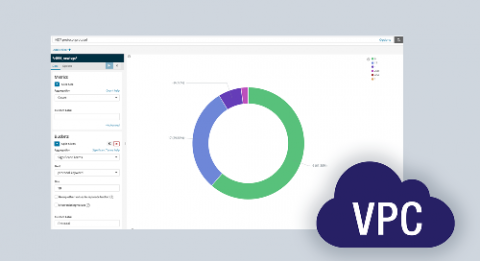
13 Security Alerts and Visualizations for VPC Flow Logs
AWS VPC Flow Logs record details about the traffic passing through your application, including requests that were allowed or denied according to your ACL (access control list) rules. It also has information about the IP addresses, and ports for each request, the number of packets, bytes sent, and timestamps for each request. This information brings deep visibility and the ability to improve your security posture over time.
Elastic SIEM for home and small business: Beats on CentOS
Hey, there. This is part five of the Elastic SIEM for home and small business blog series. If you haven’t read the first, second, and third blogs, you may want to before going any further. In the Getting started blog, we created our Elasticsearch Service deployment and started collecting data from one of our computers using Winlogbeat. In the Securing cluster access blog, we secured access to our cluster by restricting privileges for users and Beats.